How to Stay Safe – On the Move
This is the last article in my series aimed at helping you stay safe online. My goal has been to bring some clarity and give some plain-English advice on the subject of computer security. It’s a huge area and it is constantly evolving so I don’t profess to guarantee your security. If you do follow this advice, though, you will greatly reduce the chance of getting something undesirable on your device.
Wireless
Forgive me if you already know this but for clarity it is worth reiterating the meaning of the term ‘wireless’. When used in relation to computer devices wireless refers to the connection from your device (laptop/phone/tablet/Mac etc.) to a *local* device – knows as an access point (AP). It’s just a replacement for a physical connection from your device to a network. From here your connection passes onto the Internet in the same way as if you were physically connected to the network.
A wireless connection is distinct from the connection your mobile provider uses to connect you to the Internet across the mobile phone network. This is known as the Edge, 3G or 4G network.
A wireless facility will be provided to you in a distinct locality – most commonly in a café, hotel, or airport – and using one can be risky if it is not secured. The wireless signal between you and the access point you are connecting to is broadcast around you. That means that anyone with a little technical knowledge can pick up your transmission and read it. It is imperative, therefore, that the ‘conversation’ is encrypted. In this way, even if it is intercepted it can’t be decoded. It is also important that you choose an adequate level of encryption.
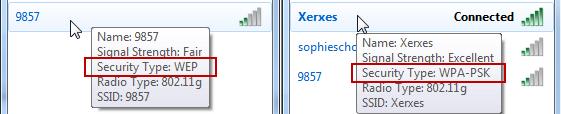
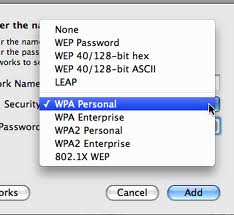
There are 2 common levels of encryption in use – WEP and WPA. WEP is not good enough and you should be extremely careful if you are connecting to a network that only offers this level of protection. We recommend WPA as a minimum and WPA2 is ideal. You may see it listed in other formats (WPA-PSK for example). The rule is as long as you see WPA then you are securely encrypted.
To determine the level of encryption offered by a wireless network you can check from your computer. It should be displayed alongside the list of available wireless networks. So for Windows XP it looks something like this:
In Windows 7 you’ll see the following:
On a Mac it’ll look more like this:
Remember that wireless security only protects the traffic passing between your device and the local access point. From the access point to the Internet your connection is subject to all the usual risks.
This level of security should also be implemented when you set up wireless on your own home network.
Mobile recommendations
Think for a moment about everything you now have on your mobile phone or tablet:
- Email, contacts, calendar
- SMS messages containing sensitive information
- Apps, music and other purchases
- Personal pictures and videos
- Automatic log in to websites e.g. facebook, linkedin
- Copies of personal and work data e.g. dropbox
If you lose your phone or have it stolen the risk to you is no longer simply the loss of information. You will also be allowing the new owner of your phone access to large parts of your personal and work life.
The most significant single action you can take is to set a passcode on your mobile device.
If you haven’t already set one up and are unsure of how to proceed then simply Google ‘passcode’ and the model of your device for a myriad of instructional guides and videos.
If you do lose your device then report it immediately. Get in touch with your IT Support Helpdesk too and in many cases they may be able to send it a remote command to wipe all data off the device. Change passwords to the online accounts that can be accessed through the device.
If you are giving your phone to someone then make sure you clean it up properly. We recommend:
- take a complete backup to your PC or Mac – N.B. a synchronisation with local software or to the cloud is not enough. You must do a full backup.
- if possible take a second backup to an alternate machine
- double check that the backup has worked. Often the easiest way to do this is to set up a restore. If the backup was successful then it will be listed to be restored from
- reset the device to factory settings
Working from an untrusted device
You need to take extra care when using an unfamiliar device. Whether provided by a friend or a company (Internet café or hotel, for example) you will never know what software is installed on that machine. A friend can reassure you that everything is secure but they may not be aware that they have an infection. Internet cafés can be particularly risky places. Personally I avoid them completely.
If you do have to use an untrusted device then be aware that everything you type could be recorded. So that means not using websites that require a login name and password.
Other stuff
External media – CDs, DVDs or USB sticks – can carry infections. So you need to check them for an infection before accessing the files they contain. Most anti-virus software these days will allow you to run a scan on attached media. This may happen automatically when you first load the media but if in doubt run a manual scan before accessing anything.
So that’s it then.
My series of articles is at an end. I hope they have been helpful and interesting. Most of all I hope they help protect you from the nasties out there on the Internet. If there is anything in this article that you would like further help with then please do not hesitate to get in touch.